We value your privacy
We use essential cookies to make this website work.
In addition, we would like to set cookies to help us understand how our website is used.We use essential cookies to make this website work.
In addition, we would like to set cookies to help us understand how our website is used.There are several types of mystery geocaches, many of which you need to solve at home before you venture out to find the geocache. This is a guide to some of the commonly used text cyphers and will help you to try and solve some of the many puzzle caches.
No, it's not got anything to do with a pork product - this was devised by Francis Bacon. The Baconian cipher is a method of steganography. Steganography is the art of writing hidden messages in such a way that no one suspects the existence of the message. For this cipher, each letter is encoded with a series of 5 characters, consisting of a number of A's and B's. If AAAAA represents the letter ‘A’, and AAAAB represents ‘B’, then AAABA would be the letter ‘C’, and so on.
However, in a text encoded with this cipher, you will rarely see these series of A's and B's. They are hidden within a text. An example is the coding through typeface, for example normal and italic letters. The normal letters might represent an A and the italic letters represent a B. By this way we can hide a secret message within apparently normal text. For example “a quick guide to ciphers.”would decode to “aabba aaaaa aabba aaaab”, which gives us “GAGB”!
For geocaching puzzles you can find examples of both plain “A B” codes and “hidden” as well.
The pigpen cipher (sometimes referred to as the Masonic cipher, Freemason's cipher, or tic-tac-toe cipher) is a geometric “simple substitution” cipher, which exchanges letters for symbols which are fragments of a grid. There are lots of different types based on this - not all of them have a dot in a box (or a “pig” in a “pigpen”) but the basic principle is always the same. An example of how pigpen might look is below - note how the letter T is always represented by the same symbol - so once you’ve got one letter, the rest become easier to work out. This is “simple substitution”.
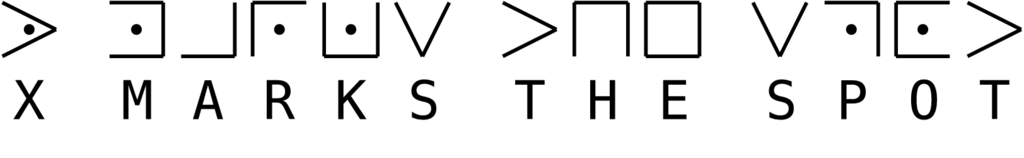
Templars code is a variation of pigpen but uses a Maltese cross as its base like this:

 The Caesar cipher (or “shift cipher”) method also uses a simple substitution encryption, but not using graphics. This means that every character is substituted by another character according to a specific system. The substitution character is determined by “rotating” the alphabet. For example, the well-known and mostly used ROT13 method shifts the alphabet by 13 positions, this results in: A=>N, B=>O etc, which we all know from the hints system used with geocaches. Every other shift from 1 to 13 is also possible. There are a number of tools on smartphones and the internet for deciphering this type of cipher.
The Caesar cipher (or “shift cipher”) method also uses a simple substitution encryption, but not using graphics. This means that every character is substituted by another character according to a specific system. The substitution character is determined by “rotating” the alphabet. For example, the well-known and mostly used ROT13 method shifts the alphabet by 13 positions, this results in: A=>N, B=>O etc, which we all know from the hints system used with geocaches. Every other shift from 1 to 13 is also possible. There are a number of tools on smartphones and the internet for deciphering this type of cipher.
Moon type was developed by Dr. William Moon, a blind Englishman living in Brighton. At age 21, after a bout of scarlet fever, Moon lost his sight and became a teacher of blind children.  He discovered that his pupils had great difficulty learning to read the existing styles of embossed reading codes, and devised his own system that would be "open and clear to the touch."
He discovered that his pupils had great difficulty learning to read the existing styles of embossed reading codes, and devised his own system that would be "open and clear to the touch."
Moon first formulated his ideas in 1843 and published the scheme in 1845. Moon is not as well-known as Braille, but it is a valuable alternative touch reading scheme for the blind or partially sighted people of any age. It’s also used by a few of those cache puzzle setters. Each symbol should be raised so it can be felt using fingers, but we can also see the system and ‘read’ it with our eyes: This is again a “simple substitution”.
The Vigenère cipher is a classic (famous) cryptography method. The cipher is easy to understand and implement, but it resisted all attempts to break it for three centuries! How clever are we?
It is a complicated version of the Caesar cipher that discussed above. You may remember then that, each letter of the alphabet is shifted along some number of places. For example, in a Caesar cipher of shift 3, A would become D, B would become E, Y would become B, and so on.
 The Vigenère cipher is like having several Caesar ciphers in sequence, each with different shift values. To encrypt, a table of alphabets can be used, termed a tabula recta, “Vigenère square” or simply a “Vigenère table”. It has the alphabet written out 26 times in different rows, each alphabet shifted cyclically to the left compared to the previous alphabet, corresponding to the 26 possible Caesar ciphers. At different points in the encryption process, the cipher uses a different alphabet from one of the rows. The alphabet used at each point depends on a repeating keyword.
The Vigenère cipher is like having several Caesar ciphers in sequence, each with different shift values. To encrypt, a table of alphabets can be used, termed a tabula recta, “Vigenère square” or simply a “Vigenère table”. It has the alphabet written out 26 times in different rows, each alphabet shifted cyclically to the left compared to the previous alphabet, corresponding to the 26 possible Caesar ciphers. At different points in the encryption process, the cipher uses a different alphabet from one of the rows. The alphabet used at each point depends on a repeating keyword.
Sounds really complicated, doesn’t it? Luckily for us, the internet has several options for tools that now can reveal these in a few moments with the right keyword - yes you still have to have the key, which is often hidden somewhere on the geocaching page. If you don’t have the right key, however, cracking it manually make take you the best part of 300 years… or you may wish to search online for tools - there’s at least one that can start to help you with that too!
Vigenère image from https://www.dcode.fr/vigenere-cipherThe Gronsfeld cipher is, just like the Vigenère cipher, a polyalphabetic substitution. Characters are replaced using different alphabetic series and a keyword is used for the encryption. The only difference is that the Gronsfeld cipher uses a numeric key - this means it is limited to 10 different cipher alphabets, corresponding to the digits 0 to 9. The Gronsfeld cipher is strengthened because its key is not a word, but it is weakened because it has just 10 cipher alphabets. It is Gronsfeld's cipher that has became widely used throughout Germany and Europe, despite its weaknesses.
Again like the Vigenère cipher you can solve these in minutes using online tools as long as you have the key, which is often hidden somewhere on the geocaching page.
A regular in geocaching puzzles, Morse is a communication code consisting of short and long signals, which are broadcasted with short intervals. In terms of geocaching, this is often, but not always, seen as dots and dashes. The signals serve as code, as singles or as groups, for characters of the Roman alphabet, arabic numbers and some punctuation signals. The short signals are represented by a . (a dit) and the long signals by a - (a dah).
is
x marks the spot
Encode and decode the words of the character Kenny from Southpark. It is a simple substitution cipher using the language of Kenny McCormick, and it’s a lot of fun to try to say out loud as well!
is
x marks the spot
How to spot when it’s being used? Just look for lots of m, p and fs in the code and it’s a good chance it could be this one.
International maritime signal flags refers to various flags used to communicate with ships. The principal system of flags and associated codes is the International Code of Signals. So you might see a puzzle cache page with a series of flags on. There are some variations of this relating to specific countries and their navies.

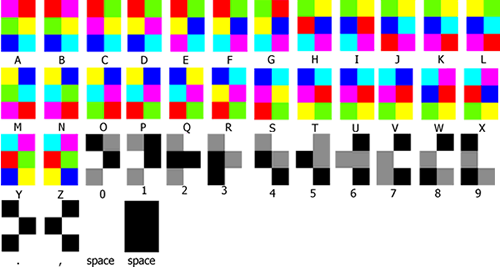 Hexahue was invented by Josh Cramer. He was inspired to come up with a unique alphabet that could substitute standard English writing for combinations of colours that were easily able to be distinguished. Hexahue colours are more "commonly" recognized colours, with "common" names, and yet they are simple to write in HTML notation. Letters are written in 2x3 squares with incrementing patterns of 6 of the colours (red, green, blue, yellow, cyan, and purple). Numbers are written with incrementing patterns of 3 of the colours (Black, Gray, White).
Hexahue was invented by Josh Cramer. He was inspired to come up with a unique alphabet that could substitute standard English writing for combinations of colours that were easily able to be distinguished. Hexahue colours are more "commonly" recognized colours, with "common" names, and yet they are simple to write in HTML notation. Letters are written in 2x3 squares with incrementing patterns of 6 of the colours (red, green, blue, yellow, cyan, and purple). Numbers are written with incrementing patterns of 3 of the colours (Black, Gray, White).
 The Colour Honey and Colour Tokki alphabets were invented by Kim Godgul in 2009 as alternative ways of writing English. They use six colours (Red, Green, Blue, Cyan, Magenta, Yellow) and different shapes to represent different letters, with each letter being represented by two colours. The scripts are similar, but use different shapes and are structured slightly differently. Tokki means rabbit in Korean.
The Colour Honey and Colour Tokki alphabets were invented by Kim Godgul in 2009 as alternative ways of writing English. They use six colours (Red, Green, Blue, Cyan, Magenta, Yellow) and different shapes to represent different letters, with each letter being represented by two colours. The scripts are similar, but use different shapes and are structured slightly differently. Tokki means rabbit in Korean.

This strange picture code is made up of red herrings representing numbers.


This cipher is shown as birds sitting on lines, it can be made up of silhouettes like below but could be birds images sitting in same position.

This type of single image stereogram has a hidden image within it, thus the name. You often have to look at the image in a certain way to see the numbers. This example says hello within it - can you see it?
Next, you might want to check out some Useful Links to Solve Geocaching Puzzles ![]()